Change the Relationship Security
-
From the Application tab, under Cube, click Cubes.
-
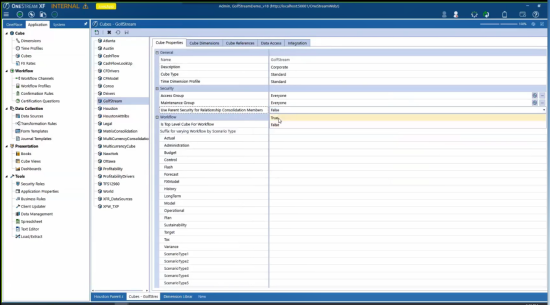
Select a Cube.
-
In the Cube Properties tab, in Use Parent Security for Relationship Consolidation Dimension Members, select True.
-
Click Save to save the cube properties. You have now changed the security model for the read or write relationship for the consolidation dimension members to be based on the security rights to the immediate parent entity.
-
Click Refresh to refresh the application.
-
In Cube Views, go to the Designer tab and click Open Data Explorer.
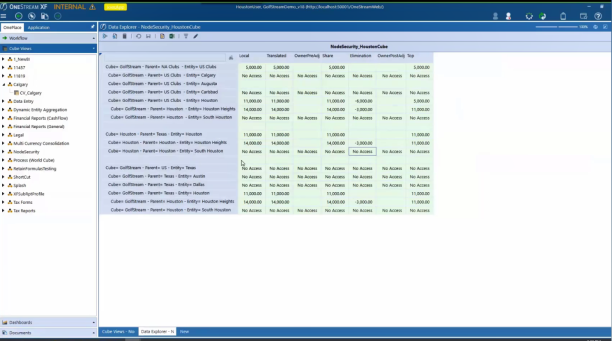
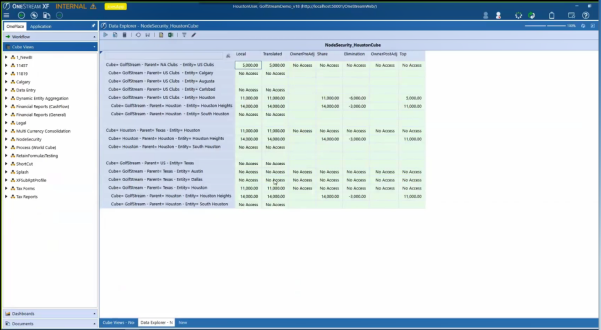
All of the security is changed.
Notice the following changes to security:
-
In the first screenshot, all the consolidation dimension members are available across Houston.
-
When you switch on the new security, in the previous screenshot, the user has rights to USClubs then looking at the Houston member there, all the consolidation dimension members are available.
-
Looking at the last group, the user has no rights to Texas, based on the NoAccess to Local and Translated. In Houston you can see the relationship members changed to NoAccess.
-
The reason why USClubs turns to NoAccess is because the user apparently has no rights to the parent NAClubs, which is not displayed on the report.
Data Security
Data security controls the overall read/write access to analytic models. There are several steps to see if you have access to data. First, it that you have the ModifyData role in the application, otherwise you do not have write access to data. Next, ensures you have either the access group or maintenance group for a cube, or you do not have access to any of the cube’s data. It will then check the scenario and Entity’s Read Data Group and Read Write Data Group to ensure access. Finally checks the Data Cell Access Security at the cube level. If you have access to the data and use Excel or any other method to import data, it ensures the entity being written to belongs to a workflow profile with an active forms channel that is not locked or certified. If any of these steps result in no access, the process stops.
-
There are several ways to guarantee data is secure. Throughout the dimensions, different security groups are available, and an administrator can decide what users belong to each group.
-
The scenario dimension has both Read Data Group and Read and Write Data Group.
-
The entity dimension uses both security groups from the scenario and adds display member group and Use Cube Data Access.
-
The display member group only refers to the member display access level, not the data access level. Use Cube Data Access is used if slice filters are being applied at the cube level to apply additional layers of security for specified security groups.
-
The account, flow, and all user-defined dimensions also use display member group.
At the cube level, more security is put in place through groups, member filters, and complex layered security. A cube slice filters a data entry form to the right member set, such as choosing the cost center in which a user can enter data. For slice filters to take effect, the user must first be granted access to the cube, scenario, and entity. Slice security cannot increase access to data that was not administered first through Users and Groups. An administrator can also lock down more than one dimension by using cube data access and can control user visibility by only giving access to certain accounts. Finally, data cell conditional input and data management access security can be used. These are not security settings but can still control how a dimension can be used for input and how a cube is modified.
Application and System Security
dimensions, cubes, business rules, data management, and File Explorer each have an access and maintenance group. OneStream recommends limiting access to these groups and assigning the screens to administrators. It is also recommended to give the ManageData role to administrators for data management and to give ManageTaskScheduler and TaskScheduler roles in Task Scheduler. The ManageFileShare role should also just be given to administrators. Anyone granted access to a folder in File Explorer has access to every file and folder through OnePlace. For FX rates, limit access by giving administrators the ManageFXRates role and selecting a set of power users.